What is JSON Web Token(JWT)?
Using JSON Web Tokens is an open, accepted method of securely representing your user’s identity during a two-party interaction.
You can use a JSON Web Token to identify your user when two systems exchange data rather than providing private credentials with each request. You can see how these methods can enhance client-server interactions by applying them to a REST API:

A sign-in request is sent by the user or client app.
In this phase, the user effectively gives the API their login, password, or sign-in credentials.
Once the request has been authenticated, the API will provide a JSON Web Token and sign it with a secret key. The client application will then receive that token back from the API.
The client app will then get the token, confirm its authenticity on its end, and utilize it for each subsequent request.
As a result, the user can be authenticated without needing to provide their credentials any longer.
How a JWT is built?
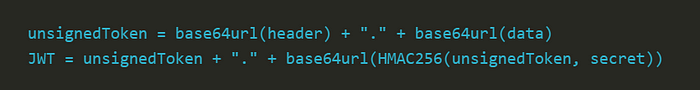
JWT consists of three parts: a header, payload, and signature.

Header: The header normally consists of two parts: the type of the token, which is JWT, and the technique that is employed, such as HMAC SHA256 or RSA SHA256. The first piece of the JWT is Base64Url encoded.

Payload: he claims can be found in the payload.
The following are some examples of registered claims: iss (issuer), exp (expiration period), sub (subject), and aud (audience). While not required, these claims are suggested to offer a collection of practical, interoperable claims. Additional parameters, like employee role, that create bespoke claims may also be included in the payload. To generate the OpenID Connect user subject, the topic claim is typically utilized. The Liberty JVM server, however, can be set up to make use of a different assertion. The payload, which makes up the second component of the JWT, is Base64Url encoded.

Signature: The encoded header and payload are signed using the signature algorithm from the header to form the signature section. The JWT’s signature is used to confirm that the issuer is who they claim to be and to make sure the message hasn’t been altered along the route.

The “Authorization” request header with the scheme “Bearer” and JWT must be included in the incoming HTTP request for a REST API call.
The system checks the token’s signature and expiration date. If the verification process is successful, the JWT’s claims are utilized to identify a legitimate OMS user, who is then used to make the REST API call.
Authorization:Bearer <Signed JSON Web Token(JWT)>
